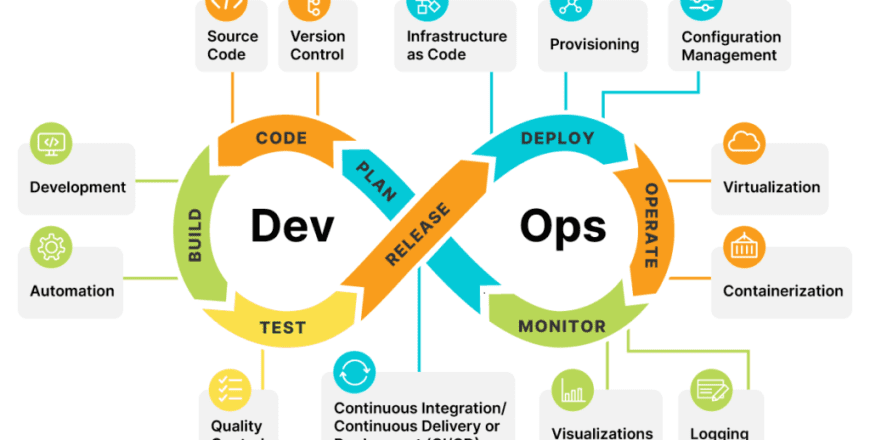
DevOps: Development and Operation of SDLC
- Description
- Curriculum
- Reviews
In the rapidly evolving world of software development, Citadel Cloud Management has established itself as a leader by offering a sophisticated and comprehensive approach to both DevOps and DevSecOps. Their focus on integrating security seamlessly throughout the software development lifecycle (SDLC) is particularly noteworthy. Here’s an in-depth review of their methodologies and tools:
1. DevOps: A Collaborative Roadmap
Citadel Cloud Management excels in defining DevOps as a collaborative roadmap for the SDLC. Their approach bridges the traditional gap between development and operations teams, fostering an environment where these integral teams work in tandem to develop, implement, and monitor software applications. This collaborative model is pivotal in enhancing operational efficiency and accelerating the delivery of high-quality software. By emphasizing cooperation and shared goals, Citadel ensures that both teams contribute to and benefit from a streamlined development process.
2. CI/CD Pipeline: Six Stages of Excellence
Citadel’s detailed breakdown of the Continuous Integration/Continuous Deployment (CI/CD) pipeline into six stages—Code, Build, Store, Prep, Deploy, and Run—provides a clear and actionable framework for managing the development lifecycle. Each stage is meticulously designed to enhance both functionality and security:
– Code: The focus here is on secure coding practices from the outset. Citadel integrates tools that ensure regular updates and proactive protection of data and applications from Day 1, embedding security deeply within the development process.
– Build: This stage emphasizes secure containerization, where code is transformed into container images that include a core OS and application dependencies. By leveraging containerization tools that manage code securely and conduct runtime dependency scans, Citadel supports agile development without compromising on security.
– Store: Citadel addresses the risks associated with off-the-shelf technologies by advocating for continual vulnerability checks. Their use of VMware Tanzu and VMware Carbon Black Cloud Container™ ensures that dependencies are securely pulled and scanned, effectively mitigating risks from third-party components.
– Prep: Prior to deployment, Citadel underscores the importance of validating application configurations against security policies. VMware Tanzu and Carbon Black Cloud Container™ play a critical role in this stage, ensuring that configurations are compliant and secure, thus setting up the deployment phase for success.
– Deploy: This stage provides a comprehensive understanding of the application’s security posture through detailed scans and vulnerability assessments. Identifying and addressing issues before production is crucial for maintaining high security standards.
– Run: Ongoing monitoring and automation in this stage ensure continuous compliance and effective risk mitigation. Citadel’s approach helps manage any vulnerabilities that surface post-deployment, maintaining a robust security posture throughout the application’s lifecycle.
3. DevSecOps: A Holistic Integration of Security
Citadel Cloud Management distinguishes DevSecOps from traditional DevOps by highlighting its comprehensive integration of security practices throughout the SDLC. Key aspects include:
– Enhanced Application Security: DevSecOps integrates automated security tools within the CI/CD pipeline, allowing for continuous testing and security audits. This proactive approach ensures vulnerabilities are promptly addressed without disrupting development cycles.
– Cross-Team Ownership: By promoting collaboration between development, security, and operations teams from the start, DevSecOps fosters a unified approach that enhances alignment and efficiency. This cross-team integration helps in building a cohesive security strategy that supports rapid and secure development.
– Streamlined Application Delivery: Security measures embedded early in the lifecycle and automated processes prevent delays caused by late-stage vulnerabilities. This integration supports fast and efficient development cycles, ensuring timely application delivery.
– Limiting Security Vulnerabilities: Automation and pre-built scanning solutions are leveraged to minimize vulnerabilities and accelerate remediation. This approach aligns with agile development practices, reducing risks and enhancing security.
4. VMware’s DevSecOps Implementation
Citadel’s use of VMware tools for DevSecOps is a standout feature. By facilitating ongoing collaboration between development, release management, and security teams, VMware’s solutions effectively enhance security and streamline the CI/CD pipeline. This comprehensive security stack provides a robust foundation for managing the SDLC securely and efficiently.
5. Infrastructure and Tools
Citadel Cloud Management’s integration of key tools and technologies—such as Terraform for infrastructure as code, Jenkins for CI/CD pipelines, Docker and Kubernetes for containerization, and Prometheus and Grafana for monitoring—demonstrates a commitment to a seamless and secure development environment. These tools collectively support modern, agile practices and ensure a resilient infrastructure.
Overall Review
Citadel Cloud Management offers a well-structured and effective approach to DevOps and DevSecOps. Their focus on secure coding practices, containerization, vulnerability management, and cross-team collaboration provides a robust framework for managing the SDLC. The integration of security throughout the CI/CD pipeline and the use of advanced tools ensure a more secure and efficient development process. For organizations aiming to enhance their DevOps practices with a strong security focus, Citadel Cloud Management delivers valuable insights and solutions that are essential for achieving modern development goals.
-
4DevOps Process and RoadmapText lesson
This curriculum is structured to give a comprehensive understanding of the DevOps process and roadmap. It is aimed at learners ranging from beginners to intermediate and advanced levels.
Overview of DevOps
DevOps is a set of practices and cultural philosophies that aim to shorten the systems development life cycle and provide continuous delivery with high software quality. DevOps is primarily a response to the challenges of traditional software development, focusing on collaboration, automation, integration, and constant feedback between software development and IT operations.
-
5Introduction and RequirementsText lesson1. If you are using windows laptop, Install GIT client on your laptop by downloading from2. You need to have an AWS account setup already.3. Create an account in GitHub or BitBucket4. Learn Agile/DevOps5. Additionally, we can download Visual Studio Code.
-
6Rancher Enterprise Kubernetes ManagementText lesson
Rancher is a powerful open-source platform for managing Kubernetes clusters, and its enterprise version comes with additional features for scalability, security, and integrations to support large-scale organizations. Rancher simplifies the deployment, scaling, and operations of Kubernetes clusters, providing a unified view across multiple clusters with strong security mechanisms.
-
7GitHub Actions, Integrations, Extensions and WebhooksText lesson
GitHub Actions is a powerful CI/CD (Continuous Integration and Continuous Delivery) tool integrated directly into GitHub. It automates the process of building, testing, and deploying applications. This platform allows you to set up workflows that respond to various events on GitHub, such as pull requests, commits, or releases.
-
8Bitbucket Jenkins IntegrationText lesson
Integrating Bitbucket Server (also known as Bitbucket Data Center) with Jenkins allows for a more streamlined Continuous Integration/Continuous Deployment (CI/CD) process. With this integration, Jenkins can automatically trigger builds based on commits to your Bitbucket repositories, and in turn, Bitbucket can display detailed build information.
-
9Launching EC2 Server, Java, Jenkins, Maven and Tomcat Setup to connect to AWS CloudText lesson
- Install Java 11
- Jenkins Setup:
- Install Jenkins
- Access Jenkins in web browser
- Create another EC2 instance for installing Tomcat and make sure you open port 8080 as well
- Tomcat Installation: Install Tomcat 9 on Ubuntu server | Setup Tomcat 9 on Ubuntu in AWS EC2
-
10Create Java Web App using Maven and setup in GitHub/Bitbucket repositoryText lessonSTEP 1: Create private repository in GitHubSTEP 2: Step # 2 Create SSH keys from your Jenkins EC2 machineSTEP 3: Upload SSH Keys in GitHubSTEP 4: Clone Repo locallyStep 5 - Create Java Web App using MavenStep 6 - Push Java Web App using Git commands into GitHub
-
11How to configure webhooks in GitHub and trigger jobs in JenkinsText lessonLet’s see how to add build a webhook in GitHub and then add this webhook in Jenkins.STEPS:-Go to your project repository.-Go to "settings" in the right corner.-Click on "webhooks."-Click "Add webhooks."-You need to enter Jenkins URL & add /github-webhook/ in the end
-
12Project build in Jenkins to automate Java build in Tomcat deploy of a WAR fileText lesson
To automate the deployment of a Java web application (MyWebApp) using Jenkins, Maven, Tomcat, and JaCoCo for code coverage, follow these detailed implementation steps. This includes configuring Jenkins, installing necessary plugins, and setting up the build and deployment pipeline. Below are the prerequisites and step-by-step instructions, including resources and GitHub links where applicable
-
13Setup SonarQube 7.7 and Integrate with Jenkins PipelineText lesson
SonarQube, also known as Sonar, is an open-source tool for continuous code quality that measures and analyzes the source code. It is built in Java, but capable of analyzing code in 20 diverse languages. SonarQube that not only checks the code and highlights the issues, but also tracks and monitors the code continuously and ensures flawless code integration as well as deployment. It can display the result of the analysis in a visually appealing way using nice charts, ‘green & red lights’, and issues list. it tries to detect bugs, code smells and security vulnerabilities. Many plugins are available to use it as part of continuous integration pipelines, including for Maven, Jenkins and GitHub.
-
14How to enable SonarQube Scanner for PL/SQL files? - Code quality check for SQL files using SonarQube - Scan sql code using SonarText lesson
How to enable open source plug-in for SonarQube.
-
15Setup SonaType Nexus 3 on RedHat Linux in EC2Text lesson
Create a new Redhat EC2 instance with small type. Choose Redhat Enterprise 8.
-
16Jenkins Nexus Integration - How to integrate Sonatype Nexus with JenkinsText lesson
How to install Nexus Artifact Uploader plug-in to integrate Nexus with Jenkins.
-
17Installing and Setup JFrog Artifactory on Ubuntu 20.04 from the Debian packages or using Docker container imagesText lesson
JFrog Artifactory is the single solution for housing and managing all the artifacts, binaries, packages, files, containers, and components for use throughout your software supply chain.
-
18Jenkins build Jobs from Slack ChannelText lesson
Install Instructions for Slack
- Get a Slack account: https://slack.com/
- Configure the Jenkins integration -
19Jenkins Scripted Pipeline for Automating Builds, Deployment and Code quality checksText lesson
- What is the Scripted Pipeline in Jenkins?
- How to Create Your Jenkins Scripted Pipeline
- Creating Your Jenkins Pipeline Script
- The Jenkinsfile
- Jenkins Scripted Pipeline Security -
20Jenkins Declarative PipelineText lesson
Jenkins declarative pipelines provide a simplified and more friendly syntax with specific statements for defining them, without needing to learn Groovy. Declarative pipelines in Sourcecode help for automatic triggers and also used as rollback strategy and disaster recovery. See: https://www.blazemeter.com/blog/jenkins-declarative-pipeline
1. Project setup in GitHub or Source Code Management
2. Jenkins and Tomcat (web container) is set up.
3. Maven is installed in Jenkins
4. Sonarqube setup and integrated with Jenkins
5. Nexus configured and integrated with Jenkins
6. Slack channel configured an integrated with Jenkins for notification -
21Jenkins Master-Slave ArchitectureText lesson
Jenkins master comes with the basic installation of Jenkins, and in this configuration, the master handles all the tasks for your build system. If you are working on multiple projects you may run multiple jobs on each and every project. Some projects need to run on some particular nodes, and in this process, we need to configure slaves.
The Jenkins master acts to schedule the jobs and assign slaves and send builds to slaves to execute the jobs.
It will also monitor the slave state (offline or online) and getting back the build result responses from slaves and the display build results on the console output. The workload of building jobs is delegated to multiple slaves.
-
22Jenkins End to End Build-Release (CI/CD) Pipeline for MyWeb and Other DevOps Tools IntegrationText lesson
Several companies already have Jenkins server setup, let us create Jenkins project, clone repository, build the CICD and deploy accordingly using Webhook trigger to slack channel
-
23Provisioning EC2 instance on AWS Cloud using TerraformText lesson
Install AWS CLI - AWS CLI Installation Steps on Windows
-
24Setup SonarQube instance using TerraformText lesson
Executing the below command after login to EC2 where you installed Terraform.
-
25How to Install Java, Maven and Jenkins during bootstrap up in EC2(AWS)Text lesson
Bootstrapping in AWS allows you to automate the initial setup of an EC2 instance by adding custom commands and scripts to the EC2 instance’s User Data section. These commands are executed when the instance starts. This is extremely useful for automating configuration tasks like installing software, setting environment variables, or configuring network settings.
-
26Suricata VM Installation and Setup on Ubuntu 20.04Text lesson
Suricata VM Installation and Setup on Ubuntu 20.04
Suricata is a Network Security Monitoring (NSM) tool that uses sets of community created and user defined signatures (also referred to as rules) to examine and process network traffic. Suricata can generate log events, trigger alerts, and drop traffic when it detects suspicious packets or requests to any number of different services running on a server. See: Suricata
Suricata is a free, open-source, robust network threat detection engine developed by the Open Security Foundation. It is capable of real-time intrusion detection, intrusion prevention, and network security monitoring. Suricata comes with a powerful rule set that inspects the network traffic and detects complex threats. It supports all major operating systems including Linux, Windows, FreeBSD, and macOS, and also supports IPv4, IPv6, SCTP, ICMPv4, ICMPv6, and GRE.
By default Suricata works as a passive Intrusion Detection System (IDS) to scan for suspicious traffic on a server or network. It will generate and log alerts for further investigation. It can also be configured as an active Intrusion Prevention System (IPS) to log, alert, and completely block network traffic that matches specific rules.
-
27CI/CD pipeline for GitHub repo using Azure DevOpsText lesson
Azure DevOps supports a collaborative culture and set of processes that bring together developers, project managers, and contributors to develop software.
-
28Ansible Setup, Configuration, Deployment and PlaybooksText lesson
Ansible is a radically simple IT automation system. It handles configuration management, application deployment, cloud provisioning, ad-hoc task execution, network automation, and multi-node orchestration. Ansible makes complex changes like zero-downtime rolling updates with load balancers easy. More information on the Ansible website.
-
29PUPPET Overview and InstallationText lesson
Puppet is a tool that helps you manage and automate the configuration of servers.
-
30LAMP STACK Overview, LAMP on Ubuntu server, LAMP on Puppet InstallationText lesson
LAMP stands for Linux, Apache, MySQL, and PHP. Together, they provide a proven set of software for delivering high-performance web applications. Each component contributes essential capabilities to the stack:
-
31MERN Stack overview, Installation on Ubuntu, Deploy a MERN Stack in AzureText lesson
The MERN stack consists of MongoDB, Express.js, React.js, and Node.js. These technologies are used to build full-stack web applications, where MongoDB handles the database, Express.js and Node.js manage the backend logic, and React.js takes care of the front-end user interface.
Here’s an in-depth step-by-step guide to deploying a MERN stack application on a virtual machine (VM) such as an Azure VM and installing the stack on Ubuntu 20.04.
-
32Docker Engine overview, Installation, Storage, Container Logs, Configuring the daemon, Networking, Logging and SecurityText lesson
Below is a detailed explanation with resource links, GitHub repositories, and implementation steps for Docker Engine installation on Ubuntu.
-
33Docker on AWS: Setup Elastic Container Registry (ECR)Text lesson
Amazon Elastic Container Registry (Amazon ECR) is a fully managed Docker container registry service provided by AWS. It enables developers to store, manage, and deploy container images. It is tightly integrated with other AWS services like Amazon Elastic Container Service (ECS) and Amazon Elastic Kubernetes Service (EKS), making it a key part of the containerized application deployment workflow.
-
34Docker using Jenkins: Docker images CICD build using JenkinsText lesson
Jenkins is an automation server often used to build and deploy applications. We’ll be cloning our code repository, build image, test image and publish image using Jenkins Pipeline.
-
35Docker Image into Nexus Registry, Configuration, Installation and UploadsText lesson
To configure Nexus 3 as a Docker private registry, you need to go through a series of steps to set up and configure Nexus 3 to store Docker images securely. Below, I will outline the entire process in detail, providing resources, links, and the necessary commands.
-
36Kubernetes Overview, Setup on Ubuntu AWS using KubeadmText lesson
Kubernetes is a powerful container orchestration tool that automates the deployment, scaling, and management of containerized applications. It allows you to manage large-scale distributed systems and ensures high availability and fault tolerance. This guide explains how to set up a Kubernetes cluster using Kubeadm on Ubuntu 18.04.
-
37Deploying Prometheus, Grafana and Helm in KubernetesText lesson
Deploying Prometheus, Grafana, and Helm in Kubernetes is a common practice for monitoring and visualizing application metrics. Below is a comprehensive guide to deploying these tools in a Kubernetes cluster, along with implementation steps, resources, and GitHub links for reference.
-
38Grafana Cloud and PrometheusText lesson
Grafana is a powerful platform for querying, visualizing, alerting, and exploring your metrics, regardless of where they are stored. It allows you to collect, monitor, and analyze various types of telemetry data such as logs, metrics, and traces. Grafana is used widely in environments such as Kubernetes clusters and cloud services like Azure and AWS, making it highly versatile. Below is an elaborate guide on setting up Grafana for monitoring, particularly in the context of Azure Kubernetes Service (AKS), as well as a breakdown of key components, tools, and resources.
-
41Introduction to Site Reliability Engineering (SRE)Text lesson
Creating a comprehensive curriculum that focuses on Big Data, AI/ML, Terraform Infrastructure, and Monitoring for a Site Reliability Engineer (SRE) is crucial for acquiring the necessary skills for working with modern infrastructure and ensuring system reliability at scale. Below is a structured curriculum with resource links, GitHub repositories (where applicable), and implementation steps for each area of focus.
-
42Big Data FundamentalsText lesson
Big Data is a term used to describe vast volumes of structured, semi-structured, and unstructured data that is too large or complex for traditional data-processing software. Learning about Big Data architectures, tools, and techniques, such as Hadoop and Spark, is crucial for handling and analyzing massive datasets. Below is an overview of the key topics, resources, and practical implementation steps to help you get started in Big Data technologies.
-
43AI/ML Fundamentals for SREs (Site Reliability Engineers)Text lesson
Objective:
Learn the basics of Machine Learning (ML) and understand how it can be applied to infrastructure management, particularly in areas such as anomaly detection, predictive maintenance, and automating operations. -
44Terraform Infrastructure as Code (IaC)Text lesson
Objective:
The goal is to learn Terraform for managing and provisioning cloud infrastructure in a repeatable, automated manner. Terraform is a popular tool used for automating the management of infrastructure resources across various cloud providers such as AWS, Azure, and Google Cloud. With Terraform, you define infrastructure as code (IaC), making it possible to provision, update, and version infrastructure in a consistent and scalable way.
-
45Monitoring & ObservabilityText lesson
Monitoring and observability are essential for maintaining and optimizing the health, performance, and reliability of applications and infrastructure in real-time. By combining metrics, logs, and traces, you gain the visibility needed to detect and resolve issues before they affect your end users.
Objective: Master tools and practices for monitoring system health, application performance, and infrastructure in real-time.
-
46Advanced SRE ConceptsText lesson
The Site Reliability Engineering (SRE) discipline aims to bring software engineering principles to infrastructure and operations, enabling teams to maintain large-scale systems in a reliable, scalable, and efficient manner. As SREs deal with production systems at scale, they focus on critical topics like incident management, disaster recovery, scalability, and cost optimization. This guide delves deeper into these advanced SRE concepts.
-
47Cloud Native and Kubernetes for SRE (Site Reliability Engineering)Text lesson
The integration of Kubernetes and containerization plays a crucial role in the modern SRE paradigm, where scalability, resilience, and automation are key principles for managing complex applications. This approach allows for more efficient resource utilization, improved application portability, and faster recovery in the event of failures.
Objective:
The objective of this guide is to help you understand how Kubernetes and containerization fit into the Site Reliability Engineering (SRE) paradigm for managing scalable and resilient applications. We’ll walk through the core concepts, key tools, and real-world implementation steps you can take to start using Kubernetes in your SRE workflows.
-
48Automating SRE TasksText lesson
Objective:
The goal is to automate and optimize SRE (Site Reliability Engineering) tasks using scripting and automation tools. These practices will improve scalability, efficiency, and response times for monitoring, alerting, provisioning, and deployment. -
49Full Stack SRE SetupText lesson
The objective of this project is to integrate various learned topics into a real-world Site Reliability Engineering (SRE) solution. The steps outlined in this document cover the full cycle of cloud infrastructure management, containerized application deployment, monitoring, anomaly detection, disaster recovery, incident management, and cost optimization. The goal is to automate deployment, scaling, and monitoring while ensuring reliability and efficiency in the system.
-
50Terraform (Overview and Tutorials)Text lesson
Configuration management is a systems engineering process for establishing consistency of a product’s attributes throughout its life. A Configuration management system allows the enterprise to define settings in a consistent manner, then to build and maintain them according to the established baselines. A configuration management plan should include a number of tools that:
-
51Terraform Setup and AWS CLI, IAM, EC2 and S3Text lesson
Terraform is an adequate tool meant for changing, versioning, or building a complete infrastructure by keeping in mind efficiency and safety. It has the potential to manage all the popular service providers and in-house solutions efficiently.
-
52Terraform Setup and AzureText lesson
-
53Terraform and GCPText lesson
-
54Terraform and Oracle CloudText lesson
-
55Azure DevOps(Board, Repos, Pipelines, Test Plans and Artifacts)Text lesson
Azure DevOps is a suite of services that support software development, providing integrated features for planning, developing, testing, deploying, and monitoring applications. Whether you’re working on a small project or managing large-scale enterprise systems, Azure DevOps helps teams collaborate efficiently, facilitating rapid development cycles and streamlined workflows. It supports a variety of Agile methodologies and integrates with multiple open-source and third-party tools to ensure that development, testing, and deployment pipelines are smooth and efficient.
-
56Azure WebApp Creation and deploymentsText lesson
Azure Web Apps provides an extensive platform to build an app in Azure without having to deploy, configure and maintain your own Azure virtual machines. We can build any web app using different languages such as ASP.NET, PHP, Node.js, and Python. Web Apps can host a User Interactive application or even a backend service like a WCF Service or Web APIs. With Web Apps, we can leverage the power of Microsoft Azure and build a multi-functional, immensely scalable, highly secured, and seamlessly accessible internet or intranet-based applications. We can also build our applications on-premise and migrate them to Azure Web Apps.
-
57Azure Kubernetes Services ClusterText lesson
Azure Kubernetes Service (AKS) simplifies deploying a managed Kubernetes cluster in Azure by offloading the operational overhead to Azure. As a hosted Kubernetes service, Azure handles critical tasks, like health monitoring and maintenance. When you create an AKS cluster, a control plane is automatically created and configured. This control plane is provided at no cost as a managed Azure resource abstracted from the user. You only pay for and manage the nodes attached to the AKS cluster.
-
58Azure DevOps Pipelines with AWS Resources IntegrationText lesson
This guide provides an in-depth procedure for integrating Azure DevOps pipelines with AWS resources, specifically using Auto Scaling Groups (ASG), Elastic Load Balancers (ELB), and other AWS services, to automate the deployment of applications across AWS and Azure environments.
Overview
As cloud workloads are becoming more hybrid, organizations are increasingly looking to avoid being locked into a single cloud provider. This integration tutorial aims to create an environment where Azure DevOps is used for CI/CD, and AWS resources like EC2, ASG, and ELB are managed and deployed automatically using Azure DevOps pipelines.
Prerequisites:
- Azure DevOps organization
- AWS Account
- A repository in GitHub or any Git-based service
- A running EC2 instance with IIS (for example, if deploying a Windows-based app)
- AWS CLI configured on your local machine
- Azure DevOps personal access token (PAT)
-
59Vulnerability Scanning and Assets ExplainedText lesson
A Vulnerability Scanner is a software tool used to identify security flaws, misconfigurations, and weaknesses in applications and network infrastructures. These tools are essential in modern cybersecurity, especially when dealing with cloud networks, as they help detect vulnerabilities that could be exploited by malicious actors. Automated vulnerability scanning tools save time and ensure consistent security practices by regularly scanning systems, services, and networks for threats.
Key Features of Vulnerability Scanners:
- Automated Security Tests: Automatically detects common vulnerabilities like SQL injection, cross-site scripting (XSS), insecure configurations, and outdated software.
- Cloud Security Integration: Many modern scanners are integrated with popular cloud services like AWS, Azure, and Google Cloud, allowing seamless detection of vulnerabilities in cloud infrastructures.
- Comprehensive Reporting: Provides detailed reports, including risk levels and remediation recommendations.
- Continuous Monitoring: Some tools provide continuous monitoring, alerting you to vulnerabilities as they are discovered.
-
60Saviynt: Identity and Access Governance SolutionText lesson
Saviynt is a cloud-based Identity Governance and Administration (IGA) platform designed to help businesses manage and secure access to sensitive resources. It provides services for identity lifecycle management, risk management, compliance, access governance, and privileged access management.
Saviynt enables businesses to have more granular control over who has access to what, and ensures that access is granted in compliance with corporate policies and regulations. It integrates with various enterprise systems, applications, and cloud environments to ensure that security and compliance requirements are met.
-
61Strata: Identity and Access Governance (IAG) SolutionText lesson
Strata Identity and Access Governance (IAG) solutions are designed to manage, secure, and govern digital identities and access across an organization's IT infrastructure. Strata IAG ensures that users have the appropriate level of access to systems, data, and applications, according to their roles, responsibilities, and policies. It helps organizations protect sensitive data while maintaining compliance with regulations such as GDPR, HIPAA, and other data privacy and protection laws.
Strata IAG solutions typically include:
- Identity Management (IDM): Management of user identities, authentication, and authorization.
- Access Control: Managing user access to resources based on roles, policies, and permissions.
- Governance: Auditing and monitoring user activities, ensuring compliance, and reporting on access permissions.
In this guide, we'll go through how to implement a Strata Identity and Access Governance solution using modern tools, frameworks, and best practices.
-
62Prisma Cloud SecurityText lesson
-
63Qualys SecurityText lesson
Qualys offers a comprehensive set of solutions for vulnerability management, compliance, and security monitoring. The Qualys Cloud Agent, as a lightweight data collector, serves a critical role in continuously monitoring and assessing hosts for various security needs. Below is a breakdown of various Qualys functionalities and how to implement them using the Qualys platform.
-
64Crowdstrike SecurityText lesson
CrowdStrike, a leading cybersecurity platform, integrates with multiple security domains like cloud security, endpoint security, identity protection, and observability/log management. These integrations enable organizations to detect, prevent, and respond to threats across various attack vectors.
This guide will help you understand how to integrate CrowdStrike with Azure Sentinel, including creating analytics rules for CrowdStrike detections, getting access to the CrowdStrike API, and integrating it with cloud services like AWS and Azure.
-
65Rapid7 Insight SecurityText lesson
Rapid7 Insight Cloud Security (formerly known as InsightAppSec or InsightVM) is a comprehensive cloud-based security solution that enables you to secure your cloud infrastructure, automate vulnerability management, and protect your digital assets. This curriculum will guide you from the basics of cloud security to mastering Rapid7’s Insight Cloud Security platform, covering its features, implementation, and best practices.
-
66Intruder Cloud SecurityText lesson
-
67Splunk Cloud SecurityText lesson
Splunk Cloud Security is an advanced cloud-based security platform designed to provide comprehensive visibility into security data across various environments. It enables organizations to monitor, investigate, and respond to security threats in real-time while taking advantage of the scalability and flexibility of the cloud.
Splunk Cloud Security integrates various security technologies, provides security operations center (SOC) capabilities, and helps organizations detect and mitigate threats quickly. It leverages Splunk's powerful data indexing and analytics engine and delivers insights through machine learning, data analytics, and correlation of security events.
In this guide, we will elaborate on Splunk Cloud Security, its capabilities, and the necessary steps to set up and use it effectively. We will also share resources such as GitHub repositories, Splunk documentation, and implementation steps.
-
68Serverless OverviewText lesson
Overview of Serverless Cloud
Serverless Cloud simplifies the development of highly scalable, secure, pay-per-use applications without the complexity of configuring cloud services. The platform handles all the infrastructure management, enabling developers to focus solely on building software. By abstracting cloud complexities like provisioning, scaling, and configuration, Serverless Cloud offers a fast, developer-friendly experience for deploying and managing applications.
-
69Serverless with AWSText lesson
-
70Serverless with Microsoft AzureText lesson
Serverless Computing is a cloud computing model where cloud providers automatically manage the infrastructure required to run the code. This eliminates the need for developers to worry about provisioning and maintaining servers, allowing them to focus more on writing code and delivering business value. Despite the name "serverless," the code still runs on servers, but the management of these servers is abstracted away from the developers.
-
71Serverless with Google Cloud PlatformText lesson
Serverless Computing on Google Cloud Platform (GCP) enables developers to focus on building applications without worrying about managing infrastructure. GCP provides a variety of serverless offerings that allow developers to write, deploy, and scale their code automatically without the need to manage servers or virtual machines. This helps businesses and developers save time and resources while optimizing cost and scaling.
-
72Serverless with Oracle CloudText lesson
Serverless Computing on Oracle Cloud Infrastructure (OCI) enables developers to build and deploy applications without the need to manage infrastructure. In a serverless environment, the cloud provider, Oracle in this case, automatically provisions, scales, and manages the infrastructure required to run the code, allowing developers to focus on writing business logic rather than worrying about servers and virtual machines.
Recent Posts
- Google Cloud Platform’s Latest Innovations: Transforming the Future of AI and Cloud Computing
- Exploring Azure’s Cutting-Edge Services in 2025: A Step Towards a Smarter Future
- What Businesses Need to Know About Quantum Computing and Big Data
- The Future of Edge AI and Its Impact on Cloud SaaS Solutions
- AI, Big Data, and Cloud SaaS: A Triple Threat for Business Growth